Application security a new approach: Software Defined Perimeter
Legacy security is not effective.
With daily news of yet another security breach, (Microsoft, Dropbox, LinkedIn, Home Depot, Yahoo and Equifax breach. it is clear that the existing application infrastructure model is hard to keep secure. Internet technology grew with some implicit assumptions of trust but as the internet scales managing these systems need a new security model. Add to that there are malicious actors exploiting these weaknesses; seeking profit, stealing corporate secrets, nation-state interference or simply damage the IT security professionals need to protect the infrastructure and data in creative ways. The new GDPR legislation is going a long way to encourage companies to be more proactive in their data protection, but what are the practical steps that can be implemented?
Traditional corporate IT infrastructure relies on VPN’s, Firewalls and software to defend against attacks such as Distributed Denial of Service (DDoS), Man in the middle, Server Query (OWASP 10) as well as Advanced Persistent Threats. However, there are a number of fundamental problems:
VPN’s – Don’t scale and once inside the network there is no control over what users can access without additional tools.
Firewalls – Are static and the more rules need to be added, the more maintenance it needs, logs are hard to analyze in real time, onboarding applications is a long process, services are not just exposed to one user.
Vulnerability/Patch management – the number of vulnerabilities is increasing, hard to prioritize and IT held hostage by old/legacy applications that are hard to upgrade.
Authentication – Multi factor vs multi-level is hard to implement according to the guidelines, ID management typically not tied to access control
Key management – Too many to effectively manage i.e user keys, device keys, encryptions keys.
So what is the solution?
With the digital threat landscape coming in all directions we need to reduce the attack surface. The Software Defined Perimeter was initially proposed by Waverley labs as an effective model for reducing the cyber attack surface.
Threats are coming from:
- External from all over the world
- Insider threats within a user group
- Insider threats, across user group boundaries
Software Defined Perimeter
This was established by a working group in 2013 with the goal of defeating cyber attacks which was comprehensive and cost effective. It took a clean sheet approach of defeating cyber attacks from multiple vectors:
To achieve their goal, the team felt that three design elements were key. First, a security model that verified identity of the user, their devices, and role before granting access to protected systems. Second, cryptographic verification to ensure the security model was being followed. And third, that the protocols to achieve items one and two be proven public domain security controls.
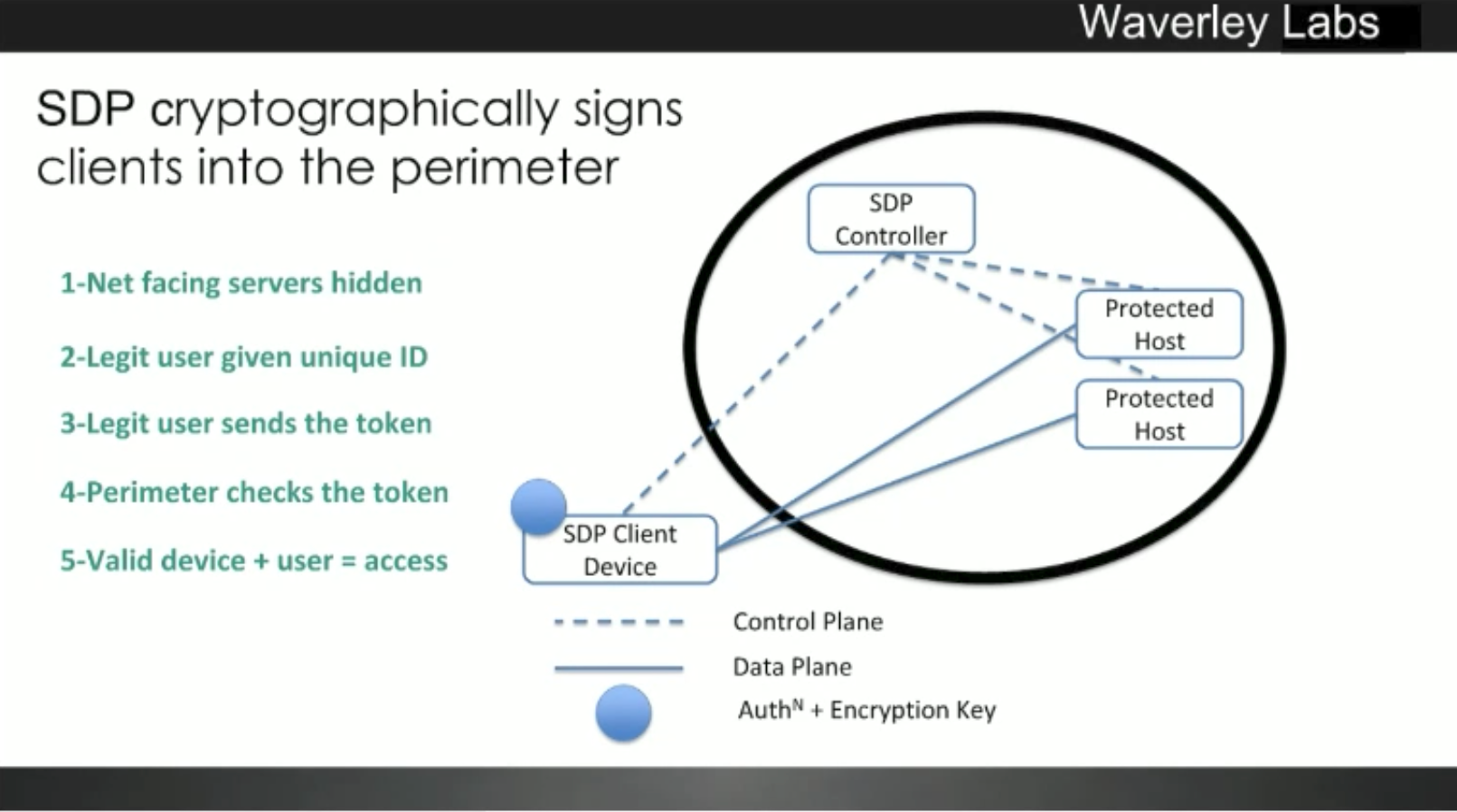
Essentially it is a cloaking scheme so that applications are not visible on the internet. Information hiding of SDP protected assets are considered “Dark” as it is impossible to scan for their presence.
There is pre-authentication of the device identity before connectivity is granted. There is pre-authorization so that access only to application servers that are appropriate for their role. Users are only given application layer access (not network.)
The protocol is extensible as it is built on proven, standards based components such as mutual, TLS, SAML and X.509 certificates
- Net facing servers are hidden
- Legit user is given unique ID
- Legit user sends the token
- Perimeter checks the token
- Valid device + user = access
Today packet filtering and load distribution techniques affect all good traffic which leads to a degradation in performance.
With SDP:
- Hosts are hidden
- Clients are coordinated with multiple perimeters
- Good packets are known
- Upstream routers informed about bad packets and can be filtered out.
Benefits of SDP
- It is Open Source and there is no licence fee and freely available from Cloud Security Alliance.
- Coca-Cola adopted it and found removing VPN and 2-factor authentication has improved the user experience.
- Users access limited to a single connection to each authorised application – eliminating malware and information theft.
- Google enabled BYOD and reduced the number of company laptops.
- Easier for Software Defined Networks to isolate authorized and unauthorize users/devices
Many thanks to Brighttalk and the cloud security alliance for making this information available on Cloud security and integration which goes into a lot more detail.