Living in a pseudo secure world.
How are you feeling about security these days?
It doesn’t seem like a week goes by without a major security vulnerability making the news. Some recent analyses by security researchers reported in Steve Gibson security now podcast show a troubling number of fundamental flaws in common technology we use every day.

Despite all the advances in technology, it seems like as we get more connected we are actually becoming less secure. Some of the core technologies that we assume to be secure are actually vulnerable through either zero-day software exploits or fundamental hardware issues.
iOS hardware vulnerabilities
A recent iPhone vulnerability called “CheckM8” read “Checkmate” has come to light. This hack affects the boot loader that is encoded in hardware (and therefore not patchable). This affects every model of iPhone from 4S up until last year’s iPhone X specifically the A5 to A11 processors (2011-2018).
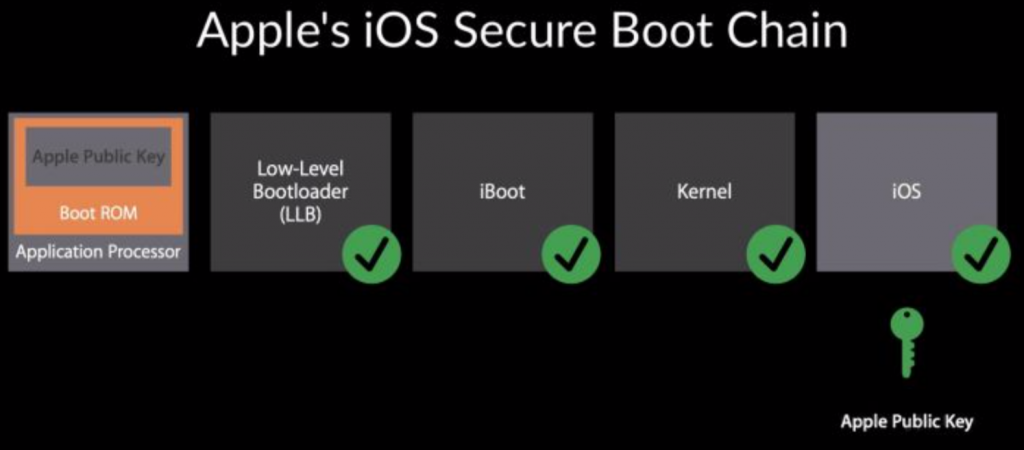
It means that hackers and security researchers now have a way to peek behind the veil of Apple’s highly secretive code base and understand the inner workings. However, Apple’s multi-layer security approach means that though there is a breach in one area it does not give access necessarily to personal data and doesn’t mean that the core security enclave is compromised but it does break down another barrier and allows a tethered compromise of an iOS device.
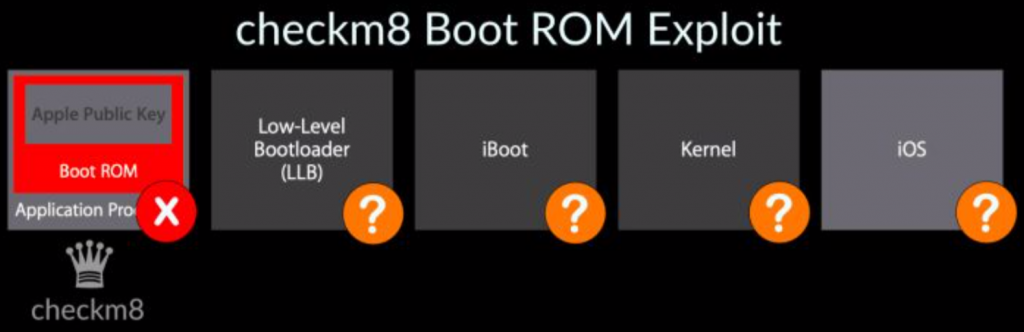
This is not a remote attack but no doubt there are other zero-days that have yet to be exposed. Like the recent example of Malware on iOS targeting Uighur minority in China.
Compromised hardware!
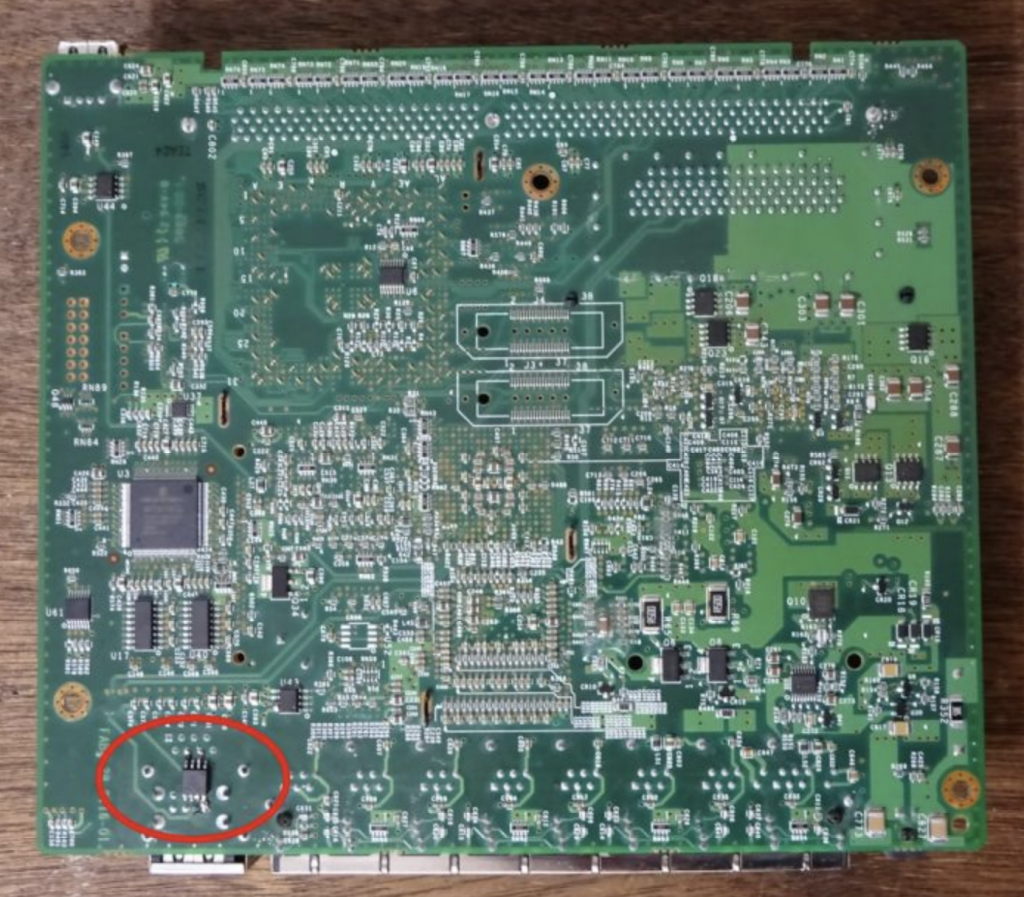
Even hardware can be compromised by the addition of small chips that allow spying on data post-manufacture and prior to delivery. A trivial exercise for any nation-state who has the ability to intercept and compromise hardware en route to a target. A security researcher recently demonstrated how easy it is to solder a small chip on a firewall to gain access to the traffic on the network.
Privilege escalation flaws
Whilst Window systems have long had privilege escalation flaws in the OS that have been exploited over the years a recent fundamental flaw in the Unix operating system that is used by millions of devices has come to light.
A buffer overflow for SUDO command, which affects every Unix, Linux and Mac systems has been found. It essentially gives the highest level of access to an affected system and there are millions of devices that use this operating system and are now vulnerable to this exploit. There are patches available to protect against this, but so many systems are not updated or not able to be updated it leaves a large body of hardware vulnerable to attack.
Security Tools like VPN
VPN (Virtual Private Network) provider, NordVPN admitted a breach in their data centre in 2018. This was just a single server and no personal data or user logs were compromised according to NordVPN. This incident was not a sophisticated hacking attempt it was simply and old account that no-one knew was there that someone started to use to gain access to the wider systems.
But recent data breaches have occurred in similar circumstances, for example, the Mariott hotel data breach was linked back to the acquisition of Starwood in 2016. There was an unaudited account from Starwood that allowed the unauthorized access to the guest database dating back to 2014.
Weaponisation of security tools
The rise of Ransomware attacks which have left several US states with little choice but to pay vast sums of money to hackers in order to regain control of their data i.e The recent case of Baltimore, Maryland attack that took down servers and is going to cost around $10 million to restore. This is a disturbing development and marks the devastating combination of criminal use of strong encryption distributed by targeted phishing attacks to gain control of whole systems.
In the UK the National Cyber Security Centre NCSC recently published the staggering number of attacks that are currently been dealt with 658 separate attacks on 900 organisations.
With hostilities and trade wars between nation-states and different ideologies set to increase I don’t see this threat coming under control anytime soon.
Bug bounty programs
As you might expect there is a healthy industry of companies looking to identify bugs like each of the major tech companies like Microsoft, Google and Apple have well paid bounty programs that incentivise people to flag vulnerabilities and make good money in doing so. There are also private companies that are springing up to address this problem like HackerOne.
How to stay secure?
As technology becomes ever more pervasive and essential, it feels that we are actually less secure. While it is true that well-configured systems can be secure, the tyranny of the default in most setups means they are not configured as they should. As well as the constant need for vigilance to keep these systems updated against the latest vulnerabilities.
I think the trends are clear, no matter how secure we think the hardware/software is there is always going to be something that lets the bad guys in. There are things that we can do to protect ourselves though.
For corporations a zero trust approach where a piece of hardware or user is considered hostile until confirmed friendly and even then access is only given as required. The iOS example above is a hardware example and most modern hardware has similar secure boot features to prevent the injection of malicious code. Other alternatives are placing strategic “honeypots” of enticing but fake data and see who tries to access them 🙂
Multi-factor authentication should be used where possible so as not to just rely on username/password combinations. But this relies on savvy users taking advantage of this technology.
For private individuals, I love Brian Kreb’s three basic rules for online safety which are simple yet profound and great advice.
- “If you didn’t go looking for it, don’t install it!”
- “If you installed it, update it.”
- “If you no longer need it, remove it.”
The main attack surface is always going to be email and internet browsing so be very vigilant where you click and where you surf. At the end of the day if you are prudent and don’t go looking for trouble it is generally safe out there so stay safe!
